The Risk Analysis View in ArchiMate helps in identifying, assessing, and managing risks within an organization. This view is crucial for aligning IT security measures with business goals and ensuring compliance with standards like ISO 27001.
Step-by-Step Guide
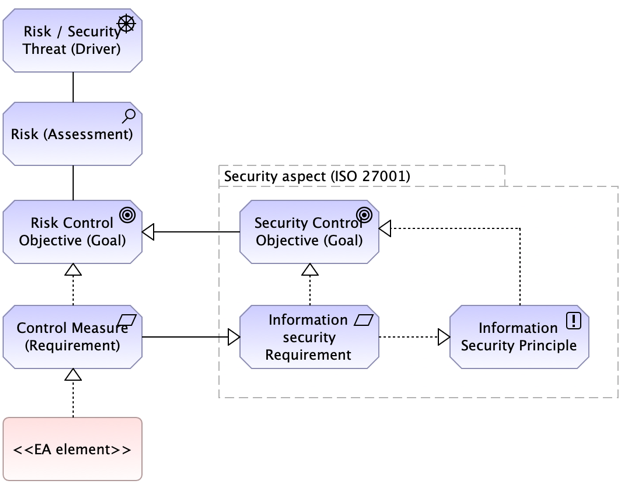
- Identify Risks
- Risk (Assessment): Represented by a purple oval with a stick figure and shield icon. This element symbolizes potential security threats to the organization.
- Assess Risks
- Risk Assessment: A purple document shape that evaluates each identified risk to understand its impact and likelihood.
- Define Control Objectives
- Risk Control Objective: A blue rectangle with ‘A’ inside, defining what needs to be achieved in terms of risk mitigation.
- Security Aspect (ISO 27001)
- Security Objective: A blue rectangle with ‘C’ inside, linked to the Risk Control Objective, showing compliance with ISO standards.
- Information Security Requirement: Another blue rectangle detailing specific requirements derived from the security objectives.
- Implement Controls
- Control Measure Requirement: A blue document shape that links back to both control objectives and requirements, illustrating that measures are based on detailed requirements stemming from broader objectives.
- Principles & Requirements Relationship
- Information Security Principle: A blue square that connects via dashed arrows with the Information Security Requirement, showing that principles guide requirement definition while also being informed by specific requirements in practice.
Symbols & Notations
- Ovals: Used for assessments or events.
- Rectangles: Represent structural elements like objectives or principles.
- Dashed Arrows: Indicate influence or realization relationships among components.
Case Study: Implementing Risk Analysis in XYZ Corporation
Introduction
XYZ Corporation, a leading financial services provider, faced increasing cybersecurity threats. To address these risks, the company decided to implement a comprehensive risk analysis framework using ArchiMate. This case study outlines the steps taken and the outcomes achieved.
Background
XYZ Corporation operates in a highly regulated industry, requiring stringent security measures to protect sensitive customer data. The company needed a structured approach to identify, assess, and manage risks effectively.
Risk Analysis View Overview
The Risk Analysis View in ArchiMate was used to map out the entire risk management process. This view includes elements such as risks, assessments, controls, and security aspects, all interconnected to depict the relationships and flow between different components of risk analysis.
Steps Taken
- Identify Risks
- Risk (Assessment): The team identified potential security threats, represented by a purple oval with a stick figure and shield icon. These risks included data breaches, phishing attacks, and insider threats.
- Assess Risks
- Risk Assessment: Each identified risk was evaluated using a purple document shape to understand its impact and likelihood. This assessment helped prioritize risks based on their severity and probability.
- Define Control Objectives
- Risk Control Objective: The team defined control objectives, represented by a blue rectangle with ‘A’ inside. These objectives aimed to mitigate identified risks and ensure the protection of sensitive data.
- Security Aspect (ISO 27001)
- Security Objective: Compliance with ISO 27001 standards was crucial. The security objectives, shown as a blue rectangle with ‘C’ inside, were linked to the risk control objectives to ensure alignment with international standards.
- Information Security Requirement: Specific requirements derived from the security objectives were detailed in another blue rectangle. These requirements guided the implementation of security measures.
- Implement Controls
- Control Measure Requirement: The team developed control measures based on detailed requirements. This element, represented by a blue document shape, illustrated the measures needed to achieve the control objectives.
- Principles & Requirements Relationship
- Information Security Principle: The principles guiding the security measures were represented by a blue square. These principles were connected via dashed arrows to the information security requirements, showing a bidirectional relationship where principles guide requirements and are informed by them.
Outcomes
- Improved Risk Management: By following the structured approach outlined in the Risk Analysis View, XYZ Corporation was able to identify and prioritize risks effectively.
- Enhanced Security Posture: The implementation of control measures based on ISO 27001 standards significantly improved the company’s security posture.
- Regulatory Compliance: The alignment with international standards ensured that XYZ Corporation remained compliant with regulatory requirements, reducing the risk of penalties and reputational damage.
Conclusion
The Risk Analysis View is essential for understanding how risks are identified, assessed, and managed within an organization. By following this structured approach, you can ensure that IT security measures are aligned with business goals and comply with recognized standards like ISO 27001.
The use of ArchiMate’s Risk Analysis View provided XYZ Corporation with a clear and structured approach to managing cybersecurity risks. This case study demonstrates the importance of a comprehensive risk management framework in protecting sensitive data and ensuring regulatory compliance.














